
Securing backend AppServices with VNET integration: Part 1
In the first part of the "Securing backend AppServices with VNET integration" tutorial, an Azure Virtual Network can be configured to isolate backend AppServices/APIs from the outside world.
Creating an Azure Virtual Network service
To create an Azure Virtual Network service, there are several properties that need to be configured during creation. The configuration consists of:
- Basics
- IP Addresses
- Security
- Review + Create
The properties are explained on a screen-by-screen.
Basics
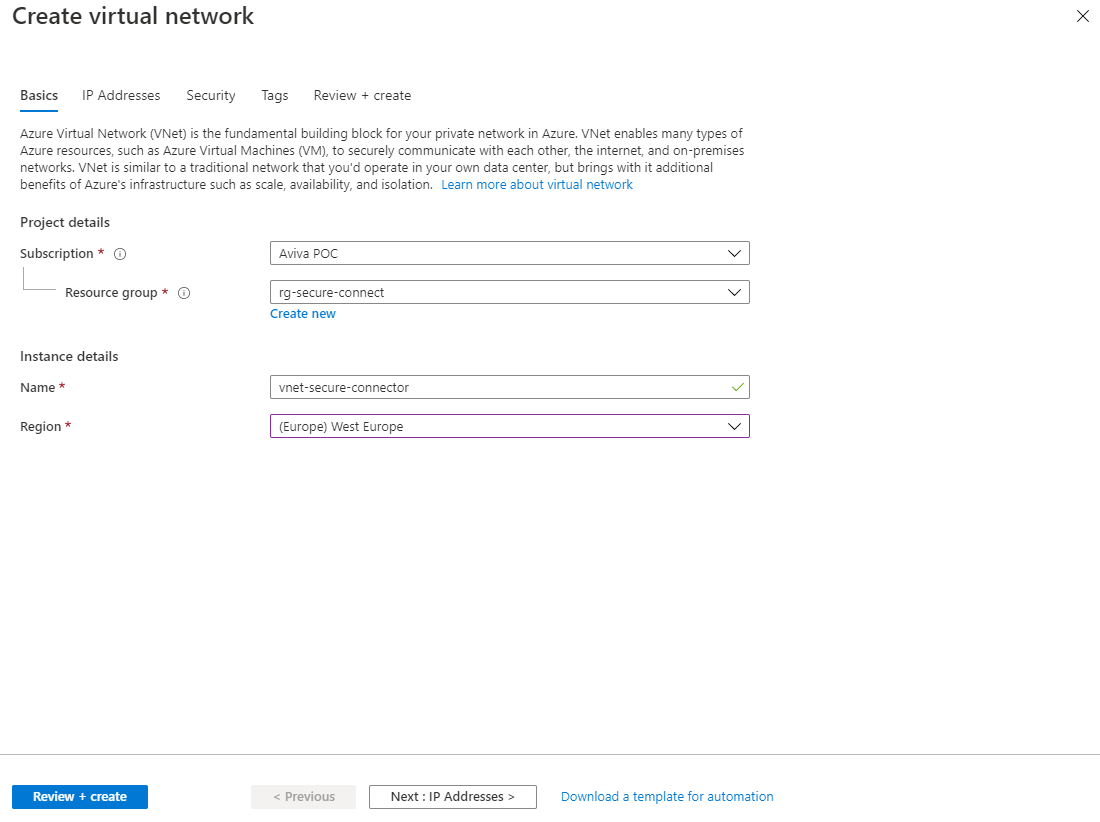
The basic properties for creating an Azure Virtual Network include:
- Subscription
Select the correct subscription where the Azure resource can register the costs incurred. - Resource group
Select the appropriate resource group to group the Azure resource into or create a new one. - Name
Give the network service a unique name. Keep a naming convention in mind. - Region
Select the region where the Azure resource should be hosted.
Then press Next: IP Addresses
IP Addresses
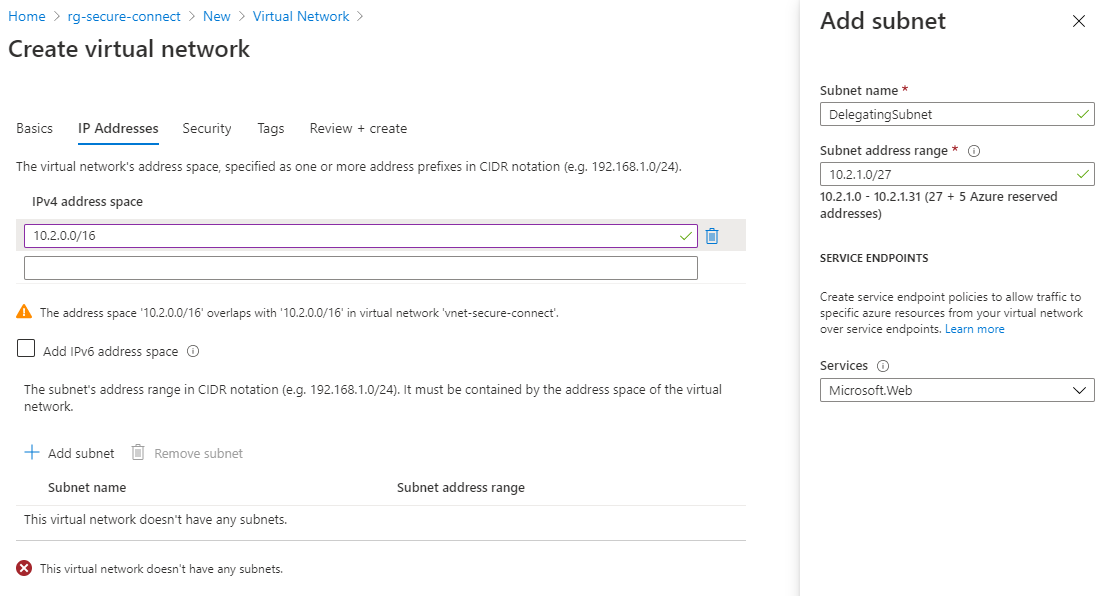
The IP Addresses screen configures the configuration of the Azure Virtual Network and subnets. The following properties can be configured.
- IPv4 address space
Enter the IP address of a private IP address space according to the RFC 1918 specification. This example uses the 10.0.0.0.0 private IP range. In the Ipv4 address space field, fill in an IP range: 10.2.0.0/16. Optional in check to also support the IPv6 protocol. This functionality can also be turned on later.
Press Add subnet to add a subnet. The properties required for this:
- Subnet name
The name of the subnet. Keep a naming convention in mind. - Subnet address range
The range of the subnet. Enter the range 10.2.1.0/27 here to connect 27 Azure resources to the virtual network. - Services
Select the endpoint Microsft.Web service here. This means that AppServices may have access to the subnet.
Add the subnet and press Next: Security.
Security
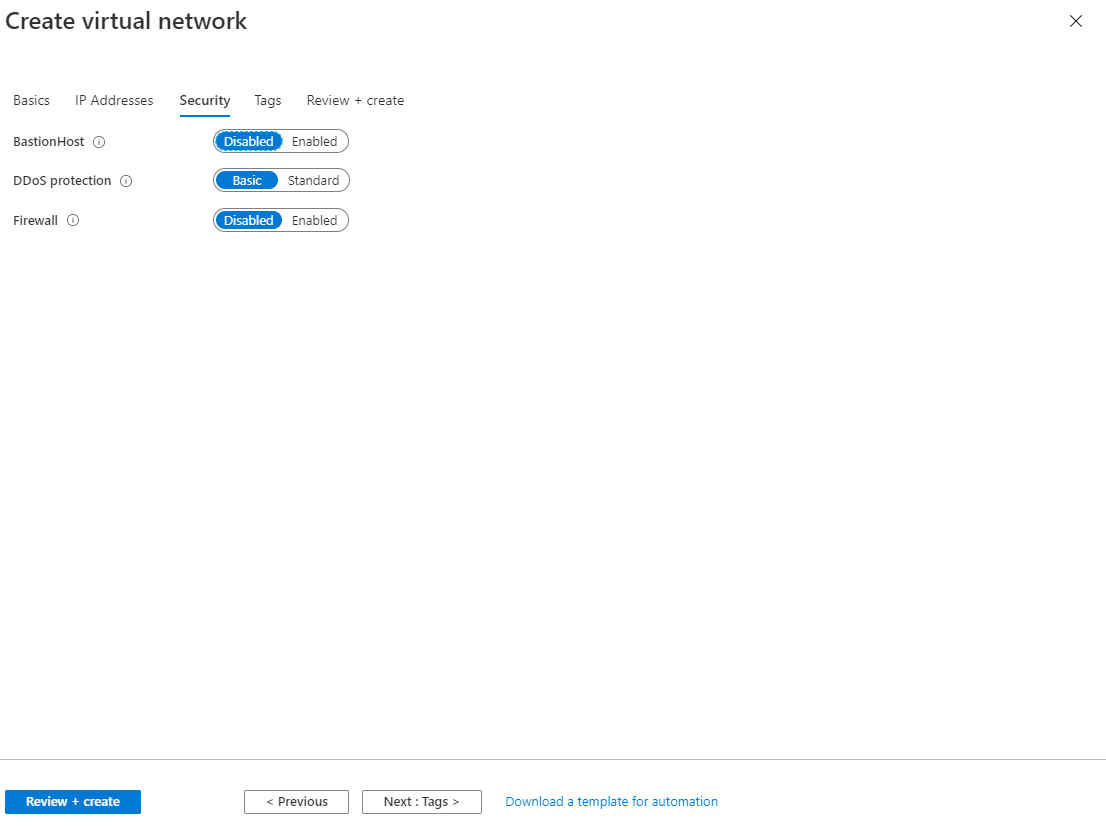
In the security tab, there are 3 properties that can be configured
- BastionHost, is standard on disabled.
- DDos protection, is standard on Basic.
- Firewall, is on disabled by default.
In this example, we keep the default values. Feel free to experiment with the security settings.
Press Next: Tags, and then press Next: Review + create. The Tags screen is skipped in this article.
Review and Create
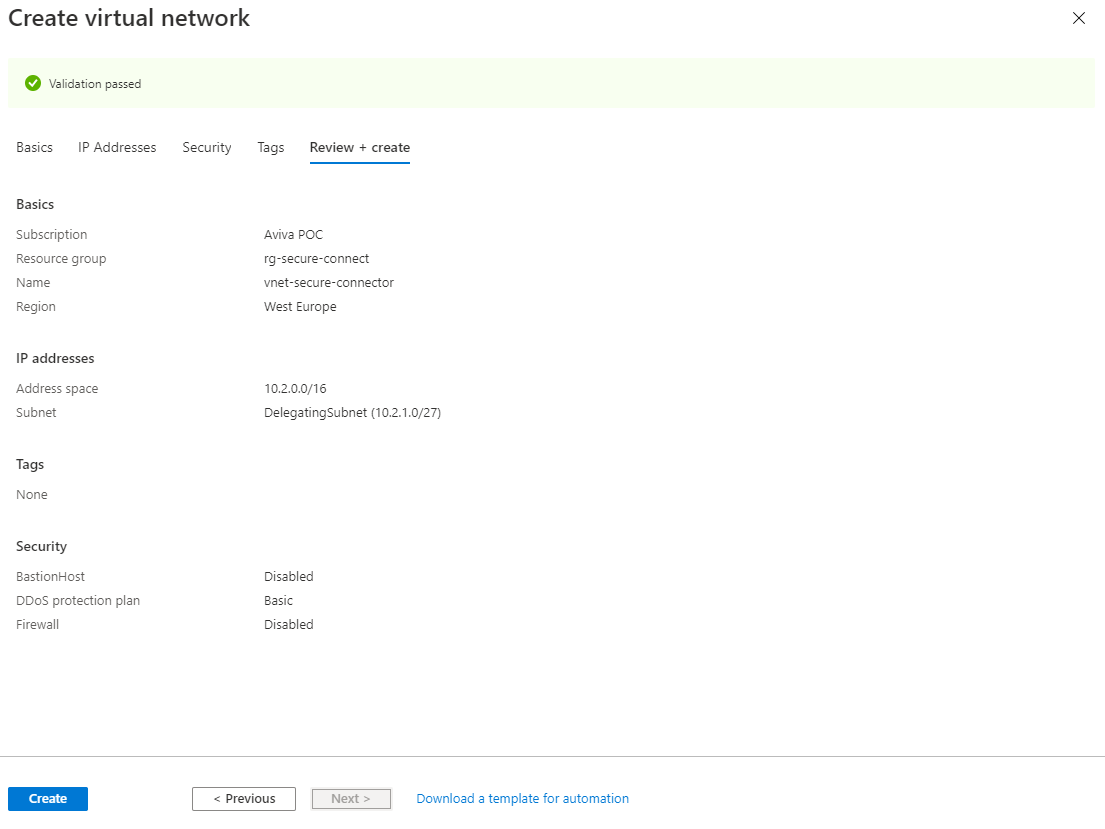
Check the configuration, and then press Create. Creating an Azure Virtual Network will take +/- 5 to 10 minutes. After creation, verify that the Azure Virtual Network is correctly configured.
The creation of the Azure Virtual Network can also be automated with PowerShell or Azure CLI. An example of an Azure CLI creation script.
# creating the resourcegroup
$resourceGroup = "rg-secure-connect"
$location = "westeurope"
az group create -n $resourceGroup -l $location
# creating the virtueal network
$vnetName = "vnet-secure-connect"
$vnetAddressPrefix = "10.2.0.0/16"
az network vnet create -n $vnetName `
-g $resourceGroup `
--address-prefix $vnetAddressPrefix
# creating and adding a delegating subnet
$subnetName = "delegatingsubnet"
az network vnet subnet create `
-g $resourceGroup `
--vnet-name $vnetName `
-n $subnetName `
--delegations "Microsoft.Web/serverFarms" `
--address-prefixes "10.2.1.0/27" `
--service-endpoints "Microsoft.Web"Handy resources
Do you have questions about securing backend AppServices? Get in touch, we'll be happy to help.
- azure
- cloud
- security

